I finally have a pair again!

Bacon + Technology
I finally have a pair again!

Assuming you have a pool, pfSense, in a mirror of disks ada0p3 and ada1p3. We want to add ada2 as a third disk to the mirror array. By default, pfSense ZFS mirror installation will use p1 (partition 1) for boot and p2 for swap.
gmirror status, zpool list, and zpool status [pool] can be used to help determine names to use below.
First we will clone one of the existing drives partition tables to the new disk:
Then we will use dd to mirror the boot partition:
We will use gmirror to clone the swap partition:
And for the pool you can either add a spare or an active third disk.
Removal Process (10-21-2023):
This guide will attempt to help you setup a WireGuard VPN on your pfSense (2.6.0) firewall / router. By the end of this you should be able to connect to your VPN with a mobile device (Android / iPhone) or laptop / PC. This will not walk you through every facet of the install as I am going to assume you know how to install packages and apps.
On your mobile device, you’ll need to install the WireGuard application from the App Store / Play Store.
Windows users will need to download the client from the WireGuard website: wireguard.com/install/
And of course, in pfSense, you’ll need to install WireGuard from the package manager.
We’ll get to configuring the clients later and focus on setting up the pfSense side first. As a means of avoiding confusion, I am also going to write the IPv6 setup separately as a lot of users will not need this.
Start by going to VPN -> WireGuard, which should bring you to the Tunnels page. On the right side, click the green “+ Add Tunnel” button.
Enable Tunnel: Make sure this is checked.
Description: whatever you want, something to identify which clients will be connecting to this tunnel, e.g. Home Tunnel
Listen Port: You can change the default if you want, leaving it blank will use the default port of 51820
Interface Keys: Make sure you click the blue Generate button. This will populate the private and public keys.
Do not click Interface Assignments or WireGuard Interface Group until after you have saved the tunnel. It will clear the public key out.
Skip down to Interface Addresses, and assign a new, local IPv4 address, such as 192.168.99.1 / 24. This ‘network’ will be what WireGuard clients use. They will still be able to communicate with your home LAN as long as you permit it in the firewall rules later on. You should have something like this (if this is your first tunnel, it will be tun_wg0 and not tun_wg1, which is fine):
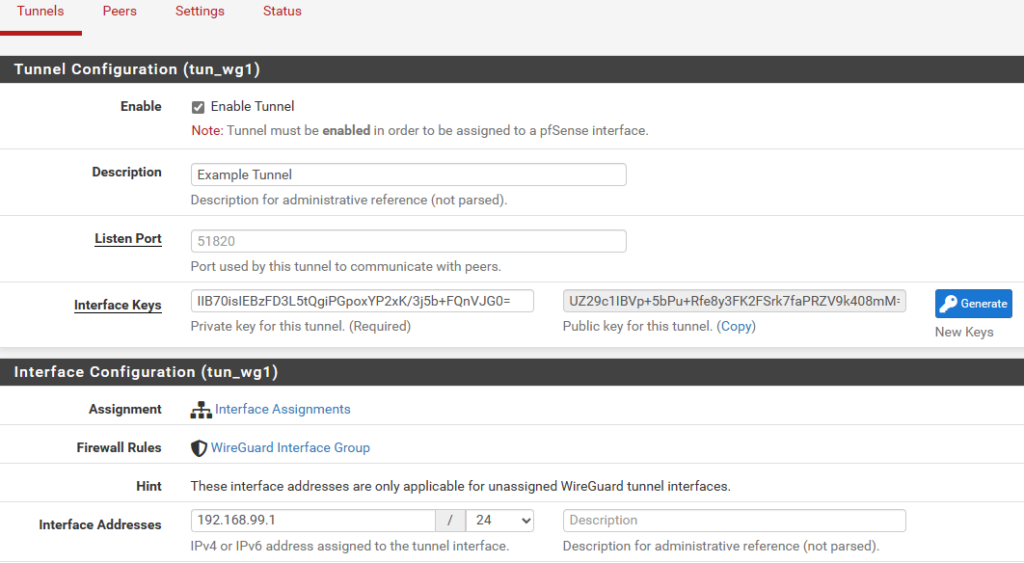
Click on Save Tunnel at the bottom of the screen. Apply changes.
Go to Interfaces -> Assignments and add your new tun_wg0 interface from the list of Available network ports. Then go into the interface itself and make sure it is Enabled. I also like to change the name to something like CLIENT_VPN. You do not need to add any firewall rules to this interface. I found if I could use IPv6 without this interface but not IPv4. So I recommend creating it.
Next, go to Firewall -> Rules. You will notice you have 2 interfaces, one called WireGuard and the other called OPT## or whatever you may have renamed it to in the interface settings (e.g. CLIENT_VPN). I have found I do not need any rules under CLIENT_VPN/the OPT interface. Officially it says to add an allow all to any rule but it never generated any traffic, and so I disabled it and have never had any problems.
The main area we want to add rules in is the WireGuard interface. For simplicity, add a new rule in the WireGuard interface to allow all IPv4 traffic, any protocol, any source/destination. For advanced configuration, this is where you will limit which clients can access what. e.g. if you assign a client 192.168.99.5, you can firewall just that IP in here.
Navigate to Firewall -> Rules -> WAN and add a new rule to allow any UDP traffic to 51820 (or your configured port). Instead of a rule, you may need to add a NAT forwarding rule instead, to allow incoming traffic to 51820 (or your configured wireguard port) to forward to the wireguard tunnel IP address (192.168.99.1 for example).
Apply changes.
First, we need to configure the client, before we can add them to the server. I realize this sounds a little backwards, but clients need to generate their own public key first, which then gets added to the server.
In the Windows client, click on the arrow beside New Tunnel and select Add empty tunnel
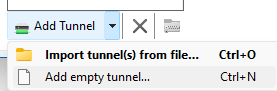
Then you’ll need to type some configuration in. The Public-key at the top of this create new tunnel wizard, we will need for later, to add into the Peer section of pfSense. Under the [Peer] section, you will need to use the public key of the tun_wg0 interface in pfSense.
A note on AllowedIPs: If you want to route ALL traffic through your VPN (lan & internet), specify 0.0.0.0/0. If you only want to use your VPN to access your LAN networks, then add your network(s) separated by commas.
I FORGOT SOMETHING IN THIS SCREENSHOT. Under [Interface], add a line called DNS = which should point to your DNS servers you want to use. In order to resolve local hostnames this part is critical. If you’re only doing IP addresses it will be less important. e.g. DNS = 192.168.99.1, 10.1.1.1.
I also just learned you can add DNS search domains to the list, so e.g. DNS = 192.168.99.1, mylan.local and mylan.local will get added to Search Domains.
[Interface]
PrivateKey = <automatically generated>
DNS = 192.168.99.1 or other DNS IP running on your network.
Address = the IP this client is allowed to connect to the VPN with
[Peer]
PublicKey = The PUBLIC KEY from the PFSENSE server tunnel
AllowedIPs = the list of IPs you want to use this VPN to connect to (e.g. your local networks only, or 0.0.0.0/0 for ALL internet traffic)
Endpoint = the public WAN IP address of your pfSense router
The server is now setup, we have our first client configured, and we can begin adding our peers. Navigate to VPN -> WireGuard. Then click on the Peers heading. Then click on the green “+ Add Peer“.
Enable: Make sure this is checked.
Tunnel: Select your tunnel interface that we created.
Description: A description of who this client is for easy reference.
Dynamic Endpoint: Leave this checked.
Keep Alive: It seems generally recommended to leave this blank, which is disabled.
Public Key: The public key from configuring the client in the previous step.
ADDRESS CONFIGURATION / ALLOWED IPs:
A lot of users get confused on this part. Generally one would assume this is where we control what networks the client is allowed to access; but that is actually done from the Firewall rules. THIS section of Allowed IPs is actually ‘which IPs is the client allowed to assign themselves on the VPN tunnel’.
So you need to decide, for every client, what their IP address will be on the VPN. You will almost always want this to be a /32 for an IPv4 and /128 for an IPv6 address. If you do it as a /24 then other clients will not be able to use the address space, and they will be unable to connect to the VPN at the same time.
So, for our first client, let’s do 192.168.99.5 / 32 as that will match what we configured above.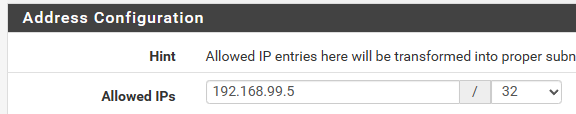
Save peer and apply changes.
You should now understand the basics to creating a WireGuard VPN. Primary notes would be that the PUBLIC KEY of the server is used in the PEER section of the CLIENT. The PUBLIC KEY of the CLIENT is used in the peer section of the SERVER. You will never use, nor should you distribute, the private keys. The ones used in this article were temporary only.
You may also want to go to Services -> DNS Resolver and make sure it is listening on your tunnel interface, so you can use it as a DNS server for the VPN clients.
Also note you will not be able to connect to the VPN from the same network that it is running on. Switch to 4G/5G mobile internet and use a hotspot to test or etc.
IPv6 is the same as above, but add an additional IP to your tun_wg0 interface (either an fd00 local address, or a fully routable WAN address from your ISP. e.g. my ISP gives me a /56 block, so I use a whole /64 block for my VPN clients). Give them an allowed IP in the peer section, configure the client to also use that IP (Address = 192.168.99.5/32, 1200:1300:1400:1500::1015/128, and also modify AllowedIPs = to include IPv6 address spaces, or ::/0 for all IPv6 routing)
I will work on cleaning up the wording and adding some additional pictures as well. But I really need to get this site migrated to a new server first.
To my approximately 0 visitors, ITBacon was down for a few days. We are back now. Apologies for any inconvenience.
Decided to run fiber in my house!

I will not use motherboard raid.
I will not use motherboard raid.
I will not use motherboard raid.
I will not use motherboard raid.
I will not use motherboard raid.
I will not use motherboard raid.
…the more I use FreeBSD, the less I want a Linux server anymore.
That’s all. Tuesday thoughts.
Oh, also I’ve changed the site to allow comments without them having to be approved first. Hello, World!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\SystemFrom an administrative command prompt, you can simply run this instead:
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1Requirements:
USBSend:
– USBSend.exe (from hp.com)
– USBSend.exe (from itbacon.com)
Newer Firmware (links updated on 12-24-2023):
– cljmfpM280fw_20230822.ENG.rfu (hp.com)
– cljmfpM280fw_20230822.nativeofficefonts.rfu (hp.com)
– cljmfpM280fw_20230822.ENG.rfu (itbacon.com)
– cljmfpM280fw_20230822.nativeofficefonts.rfu (itbacon.com)
Original Firmware I used:
– cljmfpM280fw_20220414.ENG.rfu (itbacon.com)
Disclaimer: You do this at your own choosing and risk. This is for informational purposes only.
Printer must be installed to your computer via USB cable. When the printer is in FW Update mode, you can add a new printer, local port, USB001 (or 002/003/004), and choose or browse to the m281fdw driver.
If your printer is continually rebooting itself, you will probably need to put it into Firmware Update mode, which will require taking off the left panel of the printer. This isn’t hard, but it’s not super easy either – HP sure likes to add a lot of clips to hold it together. On the back of the printer is where I recommend starting, unscrew the 1 screw holding the side panel on and begin to pry it out and away from the network port and USB port. You’ll need a flathead screwdriver or some other prying type tool, to run along the top edge of the left panel and slowly pop it out.
When you get the panel most of the way off, unsnapping it from the front was tricky, I don’t remember fully what I did. Keep unprying from the top and bottom along the sides and it should eventually come loose.
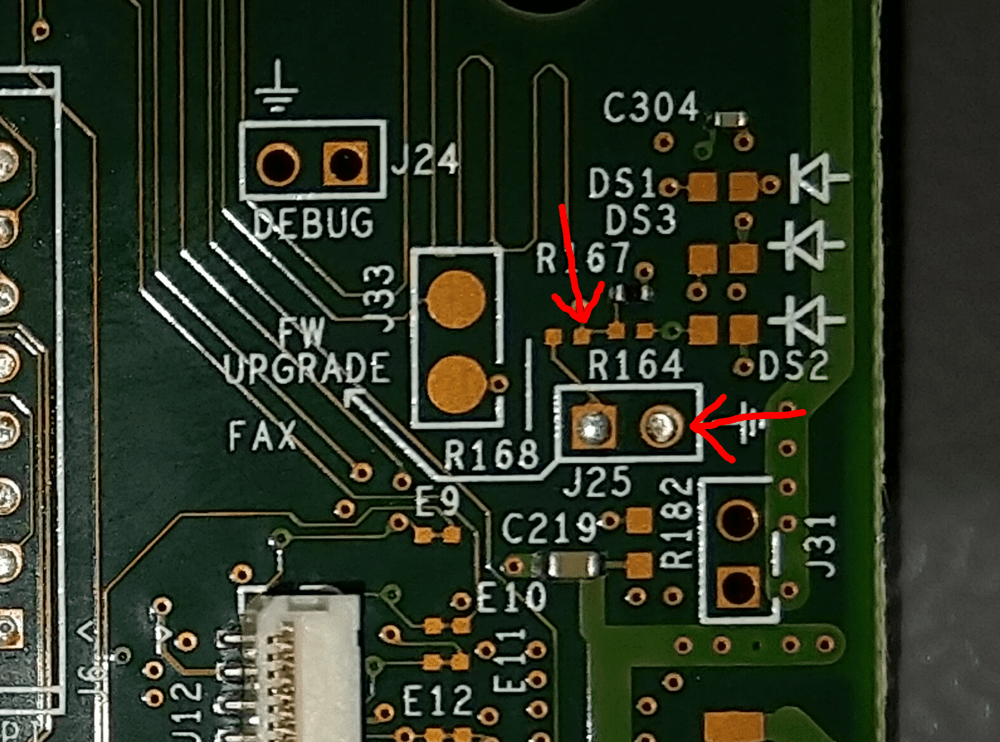
We are looking for 2 pins on the right side of the formatter board:
I used a small screwdriver to wedge between the pins while I plugged the printer in: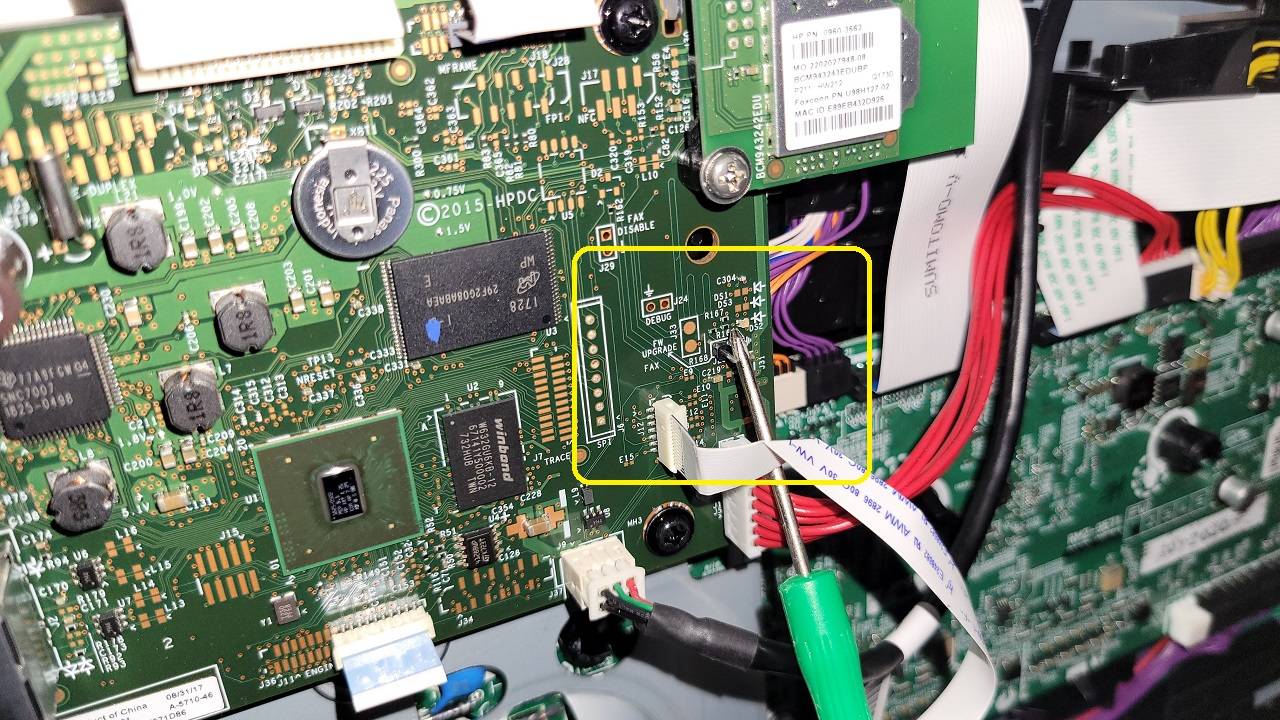
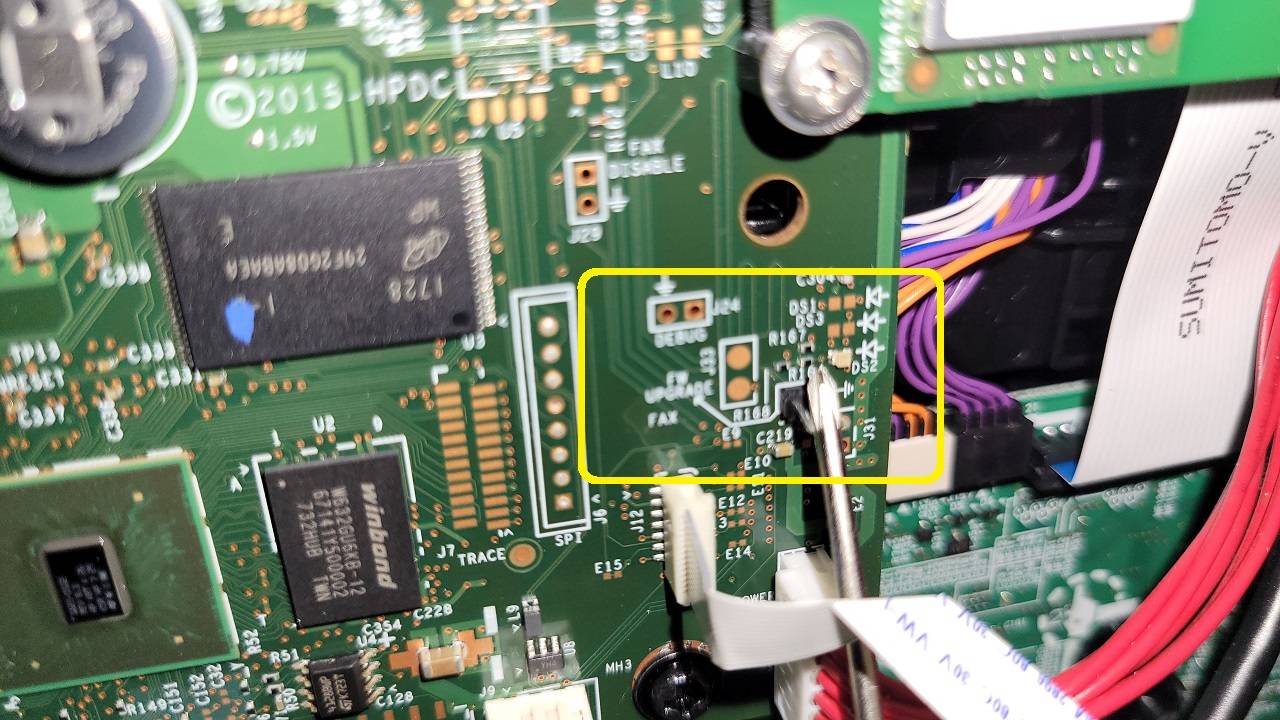
European Models do not have pins, you’ll need to jump the pads in the middle (thanks to this post)

When the printer turns on it should almost immediately come to a Ready 2 Download screen:
Remove your FW Upgrade jumper.
Launching a Command Prompt
You’ll need to start a command prompt. If they were in your downloads folder you should be able to hold shift, and right-click an empty area of the folder (don’t have any files selected) and a menu option to Open PowerShell/Command Prompt should be in the list.
Another method would be to press your Windows Key + R, which should bring up a Run box. Type cmd into the box and press enter to start a command prompt.
If the files are on your desktop, type cd Desktop to ‘change directory’ (cd) into the Desktop folder. Otherwise cd Downloads.
Now all that’s left is to use USBSend to send the RFU file to the printer (note, you must use the ENG version first, ignore the typo in screenshot – you may want to rename the rfu file to something easier to type beforehand):
The format is: usbsend filename.rfu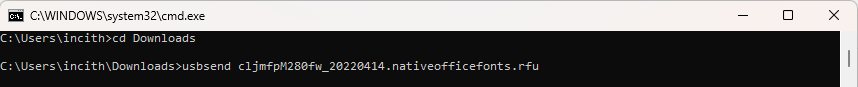
The printer display will go through Downloading, Erasing, Programming, and should end you at this screen:
Turn the printer off, and then turn it back on, and it should boot-up normally and ask you to select language etc. That’s it!
Afterwards you can download the current firmware updater to install the ‘nativeofficefonts’ firmware: M280_Series_FW_Update-20220414.nativeofficefonts.exe (from hp.com)
Update 8-13-2023: You may or may not need some or all of these commands anymore.
Below is a set of commands you can try running to help resolve issues with multiple random temporary addresses, and seemingly all of IPv6 stops working randomly. I use DHCP6 on my home network and this has helped to resolve a lot of connectivity issues for me. I don’t seem to lose IPv6 connectivity anymore.
The interface does seem to still get more than one address, which is frustrating, but probably due to router advetisements on my firewall. It only seems to use the primary one it gets from DHCP however, which is good. I have tried doing netsh int ipv6 set interface “<interface>” routerdiscovery=disabled store=persistent but, it does not persist after a reboot, and netsh int ipv6 show interface “<interface>” shows that it is enabled again. I imagine there is some registry edit that can be done, or adding it to task scheduler but, until it becomes an issue I am find that the below works for me.
I don’t know why Microsoft has made this so hard. All of my Linux and FreeBSD machines can acquire and maintain an IPv6 address forever. A singular address.
You’ll need to run these in an Administrator command prompt. You can access that by right-clicking your Start button and choosing either Command Prompt (Admin) or Windows Powershell (Admin). If you only have Powershell, once it opens, type cmd and press enter to go into a command prompt shell. Alternatively, press your Windows key or click the start button, and type cmd and press CTRL-SHIFT-ENTER once you see Command Prompt in the list (you will only need to type cmd, the start menu will select Command Prompt after a moment in ‘Best Match‘ at the top of the search results.)
netsh int ipv6 set privacy state=disabled store=active
netsh int ipv6 set privacy state=disabled store=persistent
netsh int ipv6 set global randomizeidentifiers=disabled store=active
netsh int ipv6 set global randomizeidentifiers=disabled store=persistent
Afterwards, I find going into Control Panel, (small icons) Network and Sharing Center, Change Adapter Settings, and right-click on your interface and Disable it, then Enable it with another right-click. Or you can reboot.
Sometimes, randomly, Windows Server will switch to a Private Network Profile after a reboot, or just sporadically. Usually restarting the NlaSvc service will resolve this, but I have found if it keeps happening on reboot, this will also help resolve this issue.
In order to fix this, all I needed to change was the dependencies for NlaSvc (Network Location Awareness Service). From an Administrative command prompt I ran the following:
sc config NlaSvc depend=NSI/RpcSs/TcpIp/Dhcp/EventLog/DNS/NTDS
After rebooting, my profile finally showed as a Domain network instead of a Private Network.
Windows Server 2019 is available as a free 180 day evaluation: https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-2019